Heroes Of Packet Analysis Quiz

JOIN THE HEROES OF PACKET ANALYSIS QUIZ 2021
AND WIN AN IOTA!
We all know network monitoring starts with visibility. But knowing how to use your tools is just as important. That’s why the Heroes of Packet Analysis have teamed up once again and prepared brand new challenges for you.
That’s not all: this time you can win the Wireshark Workbook from our educational partner Chappell University, and as a grand prize, an IOTA 1G! Everything you need to stay in control of your network.
Share your experience with the quiz by using #HeroesOfPacketAnalysisQuiz and #HPAQ on social media. Good luck, and may the packets be forever in your favor!

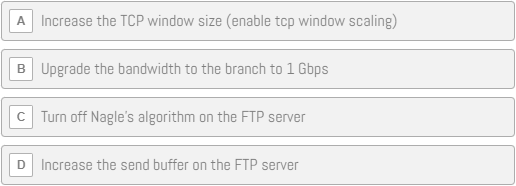
Mike Canney – Slow FTP
Users are complaining that the FTP is extremely slow to the remote office. We have a 100 Mbps link to the branch. How can we speed up this FTP?
After analyzing THIS (click to download) capture file, choose the best answer to solve this issue:
Note:
The 2021 Heroes Of Packet Analysis Quiz has ended. Keep an eye out for the next edition!
In the meantime, feel free to go through the questions for a nice challenge.
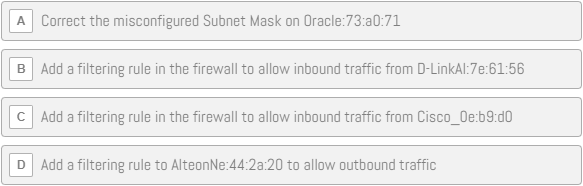
Phill Shade – Packets Never Lie!
THIS TRACE (click to download) is from a core network segment containing a firewall router, a DNS server, a router to the user’s segment, and a router to the Internet. The Internet router on this segment connects to the company’s ISP via a DSL connection. The company’s local network is not behind a NAT gateway—all internal addresses are visible from the Internet. The complaint is that when the user tries to go to the “hope.edu” website, he cannot connect to it or other websites. All users are having this problem, although the network was operating normally yesterday.
What should be the final step in solving this problem, and what are your recommendations to the Network Admin?
| Vendor ID Hex | Vendor ID Name |
| 00:10:7B | Cisco |
| 00:60:CF | AlteonNe |
| 08:00:02 | BridgeCo |
| 08:00:20 | Oracle |
| 00:80:C8 | D-LinkAI |
Note:
The 2021 Heroes Of Packet Analysis Quiz has ended. Keep an eye out for the next edition!
In the meantime, feel free to go through the questions for a nice challenge.
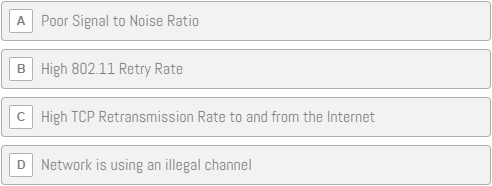
Mike Pennacchi – Poor Wi-Fi Performance
Clients are reporting that Wi-Fi performance is very slow. They can connect to the Internet, but every time they try to download files or watch videos, the load time is very slow.
You have gone out and captured the 802.11 wireless traffic to and from the wireless access point.
Here is the key information about the network:
- SSID: packetchallenge
- Passphrase: npsllc02
- IP Subnet: 192/168.88.0/24
Based on the contents of THIS TRACE FILE (35mb), which of the following is most likely the cause of the poor performance?
Note:
The 2021 Heroes Of Packet Analysis Quiz has ended. Keep an eye out for the next edition!
In the meantime, feel free to go through the questions for a nice challenge.
Chris Greer – Let’s tinker with QUIC!
QUIC supports several streams of data over a single connection. Each one of these streams has a unique stream ID.
In this QUIC connection, how many of these streams are initiated by the server?
Click HERE to download the .pcapng file for this question, along with a SSL key log to decrypt it.

Note:
The 2021 Heroes Of Packet Analysis Quiz has ended. Keep an eye out for the next edition!
In the meantime, feel free to go through the questions for a nice challenge.
Jasper Bongertz – Modbus protocol
Modbus is a protocol commonly found in industrial environments, but the conversation in THIS .pcap file seems to have a problem.
Why is that?

Note:
The 2021 Heroes Of Packet Analysis Quiz has ended. Keep an eye out for the next edition!
In the meantime, feel free to go through the questions for a nice challenge.
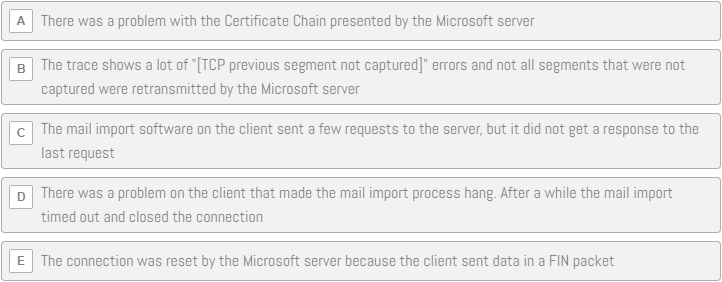
Sake Blok – Ticketing System
One of your customers is running a ticketing system that periodically performs a mail import from a Microsoft mailbox in the cloud. The customer complained that the import sometimes fails. You captured the network traffic to and from the ticketing system.
Based on the logging of the mail import, you extracted the following session that failed.
Can you tell from THIS .pcapng trace why the import failed?
Note:
The 2021 Heroes Of Packet Analysis Quiz has ended. Keep an eye out for the next edition!
In the meantime, feel free to go through the questions for a nice challenge.
Vladimir Gerasimov – Single Network Interface
You are capturing and writing data from a single network interface to disk, using custom software. At one moment, you suspect something is wrong with the captured data. To double-check, you perform a test run at 1G line rate with a hardware packet generator.
Looking at THIS trace file (200MB+ zipped), could you detect what is wrong?
This is the final question, only the participants with the most correct answers throughout the entire quiz are eligible to win the grand prize!
They will will be notified by email.
Note:
The 2021 Heroes Of Packet Analysis Quiz has ended. Keep an eye out for the next edition!
In the meantime, feel free to go through the questions for a nice challenge.
What is the Heroes of Packet Analysis Quiz?
The Heroes of Packet Analysis Quiz is an annual quiz, hosted by Profitap with the goal of challenging and educating participants in the area of packet analysis and network visibility. All Heroes of Packet Analysis have years of networking experience and are experts in their field. Join the quiz and match your skills with those of the Heroes themselves.
Who can participate?
The Contest is open to everyone worldwide who have reached the age of majority in their province or territory of residence as of the date of entry. Excluded from eligibility are the directors, employees, agents and representatives of the Sponsor, Profitap, and each of their respective parents, subsidiaries, affiliates, distributors, sales representatives, advertising and promotion agencies (collectively, the “Promotion Entities“), and members of any immediate families (defined as parents, siblings, children and spouses, regardless of where they live) or households (whether or not related) of such officers, directors, employees, agents and representatives.
How to join the Quiz?
At the start of every month a new question will be released and from all the correct answers Profitap will randomly choose one participant who will be that month’s winner.
At the end of the year when all questions are released and answered, Profitap will send one final question to a limited number of participants with the most correct answers over the complete course of the quiz and one of them will receive the grand prize!
This way even those who cannot make it every single month will have a chance to win the grand prize.
Make sure to follow Profitap and the heroes on LinkedIn, Twitter or Facebook so you do not miss a single question!
What are the Prizes?
Monthly prize: Signed book by Laura Chappell
Grand Prize at the end of the year: IOTA 1G
Every month the participant who answers the question correctly has a chance to win a signed book by Laura Chappell. From the overall pool of participants with the most correct answers there will be one who will win their very own IOTA and a chance to be our Honorary Packet Analysis Hero!
In the rare case that a single person wins multiple monthly questions Profitap will provide them with the option to receive a 50$ Amazon gift-card instead of winning multiple copies of the same book.
For more information about the quiz, check our Terms and Conditions.